Our privacy and personal data are at constant risk of getting in the hands of a sneaky world online. Encryption software is a security system that keeps all your devices free from unwanted and illegal tracking. Encryption software uses encryption algorithms to keep the data and files safe.
Search engines like Google, Yahoo tend to encrypt data. This is how they protect user information. As a result, this helps to keep the documents safe from unauthorized users. Some of the encryptions are file encryption, disk encryption, email encryption, and network encryption. This article covers the 12 best encryption software tools available in 2020.
Best Encryption Software Tools
So, what is encryption?
It is a process of encoding a message or file in a way that can be read by certain people. Using algorithms, encryption software scramble information, received by a party along with a key to decode it.
Separate encryption and decryption software tools aren’t necessary. One encryption software tool is enough to do both jobs. Process of encryption begins with an algorithmic key. This key contains the scrambled data. Separate keys help to increase the security of both encryption and decryption.
The keys are nothing but a series of complex encryption algorithms. The more complex the algorithm, the harder it is to crack. Encryption software uses bits. It ranges from 5-bits to 60-bits and more. Greater the number of bits, longer the numbers. Therefore, this ensures the complexity of the data encrypted maintains.
After the generation of the key, the encryption utility processes using the public key. The key of the encoder is never shared. As a result, this acts as an identity proof of the recipient, known as the end-to-end encryption or asymmetric encryption.
The types of encryption, based on the distribution of keys, are symmetric and asymmetric encryption.
Symmetric encryption involves the usage of one key for both encryption and decryption. As a result, this method is cost-effective and time-friendly. Using one key is, however, too risky for handling delicate data. This encryption type has become obsolete with modern internet usage. Asymmetric encryption rules out the possibility of a middleman meddling with the data. It contains data encrypted into complex multiple bits. Hence it becomes harder to crack.
1. AxCrypt
Topping the list is the encryption software tool that is widely adopted for individual usage. It is best for individuals who use the same machine every day. A128-bit or 256-bit AES encryption protects the files.
AxCrypt encryption software has been launched by AxCrypt AB, a security software company based in Stockholm, Sweden. Released in 2001, this encryption software soon became one of the best encryption tools by 2016.
AxCrypt
AxCrypt users can grant access to the secured files through a password. The encrypted information is also available on the mobile app and extended to cloud-based services such as Google Drive or Dropbox.
Business users manage passwords through a central platform. Apart from the free, limited version, the premium package costs $42/year. The business package with additional features is $87/year. A drawback of this encryption software is that the free version is used to view encrypted files on Mac. Whereas, the same free version offers more features on PC.
2. Folder Lock
Second, on the list of the most adopted encryption software is Folder Tool. This software is most suited for mobile devices. It works smoothly on any version of Windows OS. It encrypts all the stored data on your phone, including the contacts.

Folder Lock
This tool also provides anti-hacking programs, setting up false passwords, and checking illegal platform login attempts. Alongside a free version, a premium version is available at a one-time payment of $39.95. However, this tool isn’t bug-free. If there is a need to uninstall and reinstall OS, the files may be lost or corrupt.
3. IBM Guardium
Third, on the list, IBM Guardium integrates with IT management and other security management solutions to protect the data. As a scalable platform, it ensures continued structured and unstructured data traffic and enforcing policies for enterprises.
IBM Guardian
The key functional areas of Guardium’s database security system are as follows.
Data discovery and classification
It serves as the first step towards defining security policies for different data depending on its criticality and compliance requirements.
Access management
Going beyond basic access controls to database instances, this rating process focuses on more sophisticated, dynamic, policy-based access management. It is capable of identifying and removing excessive user privileges, detecting and blocking suspicious user activities, managing shared and service accounts.
Data protection
It addresses data encryption at rest. Besides, it also does so in transit, static and dynamic data masking, other technologies for protecting data integrity and confidentiality.
Vulnerability assessment
It discovers known vulnerabilities in database products, as well as complete visibility into complex database infrastructures. It detects misconfigurations, assesses and also mitigates these risks.
Monitoring and analytics
This tool monitors complete visibility in all-access, database performance characteristics and administrative actions for each instance. It provides advanced real-time analytics, anomaly detection, security information and event management (SIEM) integration.
Threat prevention
These methods of protection from cyberattacks include distributed denial-of-service (DDoS) or SQL injection, mitigating unpatched vulnerabilities and other database-specific security measures.
Performance and scalability
It is a crucial requirement for all database security solutions to be able to withstand high loads and support deployments in high-availability configurations and minimize performance overhead.
Audit and compliance
Includes centralized auditing and reporting across multiple database environments, advanced auditing mechanisms beyond native capabilities. It further enforces the separation of duties and tools for supporting forensic analysis and compliance audits.
However, the drawbacks of this tool may be worth noting too. It needs a clearer user agreement and authorization policy. It must be clear and straightforward about how exactly it reduces data risks and keeps things secure. There is a need for fewer steps to start the program, quickly and easily.
The hardware encryption capabilities of host CPUs such as Intel, PowerPC 8 AES, and SPARC and AMD AES-NI, allows encrypting local files and databases.
4. Last Pass
People are easily hacked mainly because they tend to keep the same or similar passwords for multiple services. The Last Pass, like encryption software, works as a password management application as well as two-factor authentication (2FA) app. It has a one-tap approval feature that auto-fills the credentials as well as the 2FA.
Last Pass
As a password manager, it helps to create new passwords, suggest strong passwords, store PIN codes and membership IDs. As a result, it helps in sharing passwords with others, filling addresses and card forms. It is compatible with various web-services and extended to major browsers and mobile devices for Android and iOS. The paid version of this encryption software is $36 per year. A drawback is a tedious need for a frequent change in the master password.
5. Kruptos 2
This encryption software acts as the most reliable password generator. It is a versatile file encryption software tool that encrypts files and financial data on OS, mobile devices, storage, and cloud services like OneDrive, Google Drive, Dropbox and Apple iCloud.
Kruptos 2
It is an ultra-secure technology that encrypts files using military-grade 256-bit encryption. The file shredder destroys all the sensitive files. It helps to create strong passwords with the help of built-in password analysers. The premium version is available at $40 per year.
6. CertainSafe
It is a completely cloud-based freemium encryption software tool. It provides high-quality digital cloud storage for the files online and keeps them secured from future corruptions. This service allows encrypting any form of file, images or documents online with assured security.

CertainSafe
It allows secure collaboration with teammates, clients or customers. As a result, it keeps an eye on whether the user grants access to the data or not. The data is split into multiple bits and stored in different locations. So hackers won’t be able to corrupt the data. A serious drawback is the website interface. Unlike Dropbox or Google Drive, its interface is pretty outdated and clunky. The paid premium version of this tool is $12 per month.
7. Boxcryptor
This encryption software is one of the best cloud-based software tools for non-commercial usage. It encrypts the data on your device before it syncs with the cloud, which guarantees the utmost protection. The content of the cloud is under the direct control of the user. This is because AES-256 and RSA encrypt before synchronization. This software tool uses cloud providers like Google Drive, Dropbox, etc.

Boxcryptor
It is an on-the-fly encryption. This ensures all the files are separately encrypted. As a result, the files can be decrypted separately without complete decryption of the entire folder. The pricing plan for premium members is $48 a year for personal users and $96 per year for business teams. Boxcryptor’s support system makes it chosen by everyone. During the free plan, a user is open to limited community help and extensive user guides. However, troubleshooting may pose certain problems.
8. VeraCrypt
This is an open-source disk encryption software tool that supports AES. It has the ability to create a virtual encrypted disk and mount it as a real disk. This tool encrypts a whole partition or a storage device like a hard drive. The data is read and written at the same speed with the help of parallelization and pipelining. VeraCrypt prevents cold boot attacks, gives no backdoor access, stops data leaks and prevents data theft.
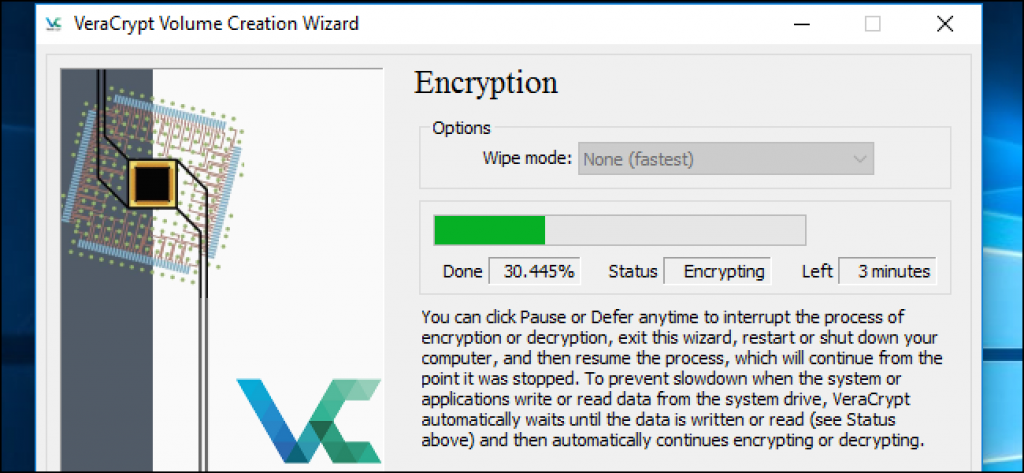
VeraCrypt
It is usable for Windows, Linux, Mac OSX. As a cherry on top, this encryption software tool is completely free. This tool is an alternative and a successor to TrueCrypt. It may be hard for a first time user to figure out the tool. The interface is neat but not self-explanatory. Users need to go through the online documentation to be familiar with the technical terms used by the VeraCrypt encryption tool in its interface.
9. CryptoExpert
This encryption software tool is available on USB flash drives to keep the keys unblocked. This tool is designed to provide secured vaults of unlimited data size. It uses one of the highly acclaimed encryption algorithms such as AES-256 encryption.
Thus providing transparent access to files and folders. It is an on-the-fly encryption software tool. Hence there is no need to wait while data is encrypted or decrypted.
CryptoExpert
Nobody can access any protected data without a password. The secure vaults appear as local drives to all Windows applications. CryptoExpert remembers all the shares and restores them on vault lock/unlock. Therefore it is possible to protect the keys on a USB flash drive by using a single Master Password.
The unlock vaults are located on remote computers over LAN. Any available drive letters are assigned to unlocked vaults. It helps to create an unlimited number of secure vaults. It is most compatible with 32-bit and 64-bit editions of Windows 10, 8, Windows 7.
10. NordLocker
NordLocker started as a simple encryption software tool. Today it retains the originality, in addition to added encrypted cloud storage. NordLocker basically encrypts everything, whether photos or spreadsheets outlining the company finances. It means if someone gains access to your computer or your hard drive, they won’t be able to figure out files inside NordLocker. It can be possible if a person has hold of the master password.
Granting permission can allow individual lockers to share data with anyone securely. All they need to do is sign up and install the app. This isn’t as convenient as sharing a file from a cloud storage service, but worthy inside your business or family. The storage space is up to 3GB of data for free. It is probably not enough to save all of your data. However, it could protect and share your most important files.

NordLocker
If one needs to encrypt data and save it to the cloud, then the prices aren’t prohibitive. That cloud stores files that can be securely synced between computers too. During file encryption, files are dragged and dropped on to NordLocker window, or picked through Finder or File Explorer. NordLocker speeds up the encryption process and the necessary uploading.
It deploys the modern-day Argon2, AES256, and ECC encryption protocols that the security community is fond of. Hence it takes the encryption seriously. No one can decrypt the files without the master password or recovery code. The premium version is $7.99 or £6.15 per month, and the annual pay is $47.88 or £36.87. This provides a generous amount of 500GB of secure cloud storage.
11. Symantec
This encryption software suits mid-sized companies. Symantec Endpoint Protection was first published in September 2007, called version 11.0. It is the result of merging several security software products. It included Symantec Antivirus Corporate Edition 10.0, Sygate Enterprise Edition, Network Access Control, and Client Security. Other features include blocking data transfers to unauthorized device types, such as Bluetooth devices or USB flash drives.
A cloud version of Endpoint Protection was released in September 2016, followed by version 14. This version incorporated machine learning technology to find patterns in digital data indicative of the presence of a cyber-security threat. It further incorporates performance improvements and memory explicit mitigation.

Symantec
Symantec Endpoint Protection includes intrusion prevention, anti-malware features and firewall. This tool has features typical of data loss prevention software. The server running Windows, Linux, or macOS, has this tool installed in it.
Since it prevents unapproved programs from running, it applies to firewall policies that block or allow network traffic. This tool allows the IT department to modify security policies for each department, such as programs or files to exclude from antivirus scans. However, it does not manage mobile devices directly. Moreover, it treats them as peripherals that protect the computer from any malicious software on the mobile device.
12. 7-Zip
It is a zip program that unzips files and encrypts them securely. It is a free program that was first developed and released in 1999. This encryption software tool is usable from a command-line interface as well as through a graphical user interface. It uses a 256 bits AES cypher for encryption.
7-Zip
Hence, it allows using backups on removable media such as writable CDs and DVDs. It is usable as orthodox file manager when used in dual panel mode. It contains multiple-core CPU threading. This tool unpacks archives with corrupted filenames and renames the files as required. It creates archives. Its Windows version comes with its own GUI. However, p7zip tends to use the GUI of the Unix/Linux Archive Manager.
Concluding
This article provides an analytic insight into the most wanted encryption software tools that are on high demand as of 2020. The pandemic is causing major shifts in work. Hence it is important to encrypt all personal and professional data. Making investments on some of the best-known encryption software is thus necessary. I hope this article answers all the queries regarding the encryption and the software tools used.

No Responses